Search the Community
Showing results for tags 'backdoors'.
-
For weeks now, unidentified threat actors have been leveraging a critical zero-day vulnerability in Palo Alto Networks’ PAN-OS software, running arbitrary code on vulnerable firewalls, with root privilege. Multiple security researchers have flagged the campaign, including Palo Alto Networks’ own Unit 42, noting a single threat actor group has been abusing a vulnerability called command injection, since at least March 26 2024. This vulnerability is now tracked as CVE-2024-3400, and carries a maximum severity score (10.0). The campaign, dubbed MidnightEclipse, targeted PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 firewall configurations with GlobalProtect gateway and device telemetry enabled, since these are the only vulnerable endpoints. Highly capable threat actor The attackers have been using the vulnerability to drop a Python-based backdoor on the firewall which Volexity, a separate threat actor that observed the campaign in the wild, dubbed UPSTYLE. While the motives behind the campaign are subject to speculation, the researchers believe the endgame here is to extract sensitive data. The researchers don’t know exactly how many victims there are, nor who the attackers primarily target. The threat actors have been given the moniker UTA0218 for now. "The tradecraft and speed employed by the attacker suggests a highly capable threat actor with a clear playbook of what to access to further their objectives," the researchers said. "UTA0218's initial objectives were aimed at grabbing the domain backup DPAPI keys and targeting active directory credentials by obtaining the NTDS.DIT file. They further targeted user workstations to steal saved cookies and login data, along with the users' DPAPI keys." In its writeup, The Hacker News reported that the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added this flaw to its Known Exploited Vulnerabilities (KEV) catalog, giving federal agencies a deadline of April 19 to apply the patch and otherwise mitigate the threat. "Targeting edge devices remains a popular vector of attack for capable threat actors who have the time and resources to invest into researching new vulnerabilities," Volexity said. "It is highly likely UTA0218 is a state-backed threat actor based on the resources required to develop and exploit a vulnerability of this nature, the type of victims targeted by this actor, and the capabilities displayed to install the Python backdoor and further access victim networks." More from TechRadar Pro North Korean hackers are posing as job interviewers - don't be fooledHere's a list of the best firewalls around todayThese are the best endpoint security tools right now View the full article
-
- security flaws
- python
-
(and 2 more)
Tagged with:
-
Executive Summary On March 29, 2024, developer Andres Freund reported the discovery of a backdoor in XZ Utils, affecting v5.6.0 and 5.6.1. XZ Utils, which provides compression tools for the .xz format, is included in a wide range of Linux distributions and projects. Tracked by CVE-2024-3094, this backdoor gives a specific attacker Remote Code Execution … Read More The post Balbix Guide to XZ Utils Backdoor appeared first on Security Boulevard. View the full article
-
A high-severity vulnerability has been recently discovered in certain D-Link Network Attached Storage (NAS) instances which could be used to run malicious code, steal sensitive data, and mount denial-of-service (DoS) attacks. Cybersecurity researcher Netsecfish, who discovered the flaw, found multiple instances of D-Link’s NAS devices have an arbitrary command injection flaw in the “system” parameter, and a hardcoded account that can be used to access the device. As a result, hackers can run commands as they please: "Successful exploitation of this vulnerability could allow an attacker to execute arbitrary commands on the system, potentially leading to unauthorized access to sensitive information, modification of system configurations, or denial of service conditions," the researcher said. No patch The vulnerability is tracked as CVE-2024-3273. Apparently, there are roughly 92,000 of these D-Link NAS devices in use today, meaning that the attack surface is relatively large. Multiple models are affected, including: DNS-320L Version 1.11, Version 1.03.0904.2013, Version 1.01.0702.2013; DNS-325 Version 1.01; DNS-327L Version 1.09, Version 1.00.0409.2013; and DNS-340L Version 1.08. Unfortunately, the patch is not coming. These devices, D-Link confirmed to BleepingComputer, are way past their end of life, and as such will not be fixed. The company released a security bulletin, and urged its customers to replace the devices with newer versions as soon as possible. "All D-Link Network Attached storage has been End of Life and of Service Life for many years [and] the resources associated with these products have ceased their development and are no longer supported," the spokesperson told the publication. "D-Link recommends retiring these products and replacing them with products that receive firmware updates." Even those that receive firmware updates should never be exposed to the internet as cybercriminals see them as valuable targets. More from TechRadar Pro UK government releases new cloud SCADA security guidance for OTHere's a list of the best firewalls around todayThese are the best endpoint security tools right now View the full article
-
Vulnerability Overview Recently, NSFOCUS CERT detected that the security community disclosed a supply chain backdoor vulnerability in XZ-Utils (CVE-2024-3094), with a CVSS score of 10. Since the underlying layer of SSH relies on liblzma, when certain conditions are met, an attacker can use this vulnerability to bypass SSH authentication and gain unauthorized access on the […] The post XZ-Utils Supply Chain Backdoor Vulnerability Updated Advisory (CVE-2024-3094) appeared first on NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.. The post XZ-Utils Supply Chain Backdoor Vulnerability Updated Advisory (CVE-2024-3094) appeared first on Security Boulevard. View the full article
-
- backdoors
- supply chains
-
(and 1 more)
Tagged with:
-
... Read more » The post xz backdoor Part 2: On the Importance of Runtime Security in the Age of OSS Backdoors appeared first on Deepfactor. The post xz backdoor Part 2: On the Importance of Runtime Security in the Age of OSS Backdoors appeared first on Security Boulevard. View the full article
-
- backdoors
- oss backdoors
-
(and 1 more)
Tagged with:
-
xz is a widely distributed package that provides lossless compression for both users and developers, and is included by default in most, if not all, Linux distributions. Created in 2009, it has since released numerous versions. As an open-source project, it is available on GitHub. However, as of the time of writing this article, attempting […] The post A Deep Dive on the xz Compromise appeared first on TuxCare. The post A Deep Dive on the xz Compromise appeared first on Security Boulevard. View the full article
-

xz-utils xz Utils Backdoor
Security Boulevard posted a topic in Security, Governance, Risk & Compliance
The cybersecurity world got really lucky last week. An intentionally placed backdoor in xz Utils, an open-source compression utility, was pretty much accidentally discovered by a Microsoft engineer—weeks before it would have been incorporated into both Debian and Red Hat Linux. From ArsTehnica: Malicious code added to xz Utils versions 5.6.0 and 5.6.1 modified the way the software functions. The backdoor manipulated sshd, the executable file used to make remote SSH connections. Anyone in possession of a predetermined encryption key could stash any code of their choice in an SSH login certificate, upload it, and execute it on the backdoored device. No one has actually seen code uploaded, so it’s not known what code the attacker planned to run. In theory, the code could allow for just about anything, including stealing encryption keys or installing malware... The post xz Utils Backdoor appeared first on Security Boulevard. View the full article -
As sure as long weekends arrive in the western world, so too does news of new supply chain attacks. The easter bank holidays were no exception, with the discovery of a targeted attack against the popular XZ compression utility seen in many linux distributions such as fedora, debian to name a few. The post CVE-2024-3094 The targeted backdoor supply chain attack against XZ and libzma appeared first on Security Boulevard. View the full article
-
Overview NSFOCUS CERT recently detected that a backdoor vulnerability in XZ Utils (CVE-2024-3094) was disclosed from the security community, with a CVSS score of 10. Because the SSH underlying layer relies on liblzma, an attacker could exploit this vulnerability to bypass SSH authentication and gain unauthorized access to affected systems, allowing arbitrary code execution. After […] The post XZ Utils Backdoor Vulnerability (CVE-2024-3094) Advisory appeared first on NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.. The post XZ Utils Backdoor Vulnerability (CVE-2024-3094) Advisory appeared first on Security Boulevard. View the full article
-
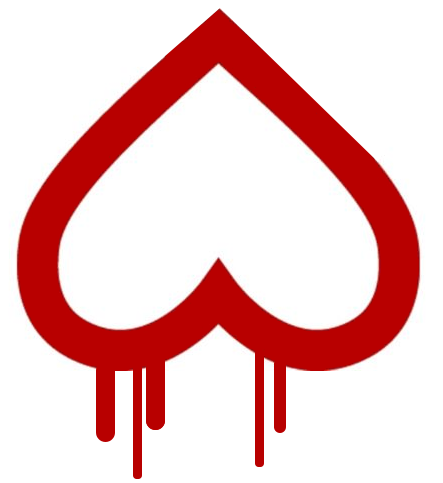
On Friday March 29, Microsoft employee Andres Freund shared that he had found odd symptoms in the xz package on Debian installations. Freund noticed that ssh login was requiring a lot of CPU and decided to investigate leading to the discovery. The vulnerability has received the maximum security ratings with a CVS score of 10 and a Red Hat Product Security critical impact rating. Red Hat assigned the issue CVE-2024-3094 but based on the severity and a previous major bug being named Heartbleed, the community has cheekily named the vulnerability a more vulgar name and inverted the Heartbleed logo. Luckily the vulnerability has been caught early Red Hat wrote: "Malicious code was discovered in the upstream tarballs of xz, starting with version 5.6.0. Through a series of complex obfuscations, the liblzma build process extracts a prebuilt object file from a disguised test file existing in the source code, which is then used to modify specific functions in the liblzma code. This results in a modified liblzma library that can be used by any software linked against this library, intercepting and modifying the data interaction with this library." The malicious injection can be found only in the tarball download package of xz versions 5.6.0 and 5.6.1 libraries. The Git distribution does not include the M4 Macro that triggers the code. The second-stage artifacts are present in the Git repository for the injection during the build time, if the malicious M4 macro is present. Without the merge into the build, the 2nd-stage file is innocuous. You are recommended to check for xz version 5.6.0 or 5.6.1 in the following distributions and downgrade to 5.4.6. If you cannot you should disable public facing SSH servers. More from TechRadar Pro Best managed VPS serversCheck out our top picks for best managed WordPressScalaHosting review View the full article
-
The Mend.io research team detected more than 100 malicious packages targeting the most popular machine learning (ML) libraries from the PyPi registry. The post Critical Backdoor Found in XZ Utils (CVE-2024-3094) Enables SSH Compromise appeared first on Mend. The post Critical Backdoor Found in XZ Utils (CVE-2024-3094) Enables SSH Compromise appeared first on Security Boulevard. View the full article
-
Forum Statistics
43.4k
Total Topics42.8k
Total Posts
.png.6dd3056f38e93712a18d153891e8e0fc.png.1dbd1e5f05de09e66333e631e3342b83.png.933f4dc78ef5a5d2971934bd41ead8a1.png)